Payment Gateway Security Standards are crucial in today’s digital age. They protect both businesses and customers during online transactions.
In the world of e-commerce, ensuring secure payment processing is vital. Customers entrust their sensitive information to businesses, expecting it to be safe. Payment Gateway Security Standards are the backbone of this trust. These standards include various measures and protocols designed to safeguard data during online transactions.
By adhering to these standards, businesses can prevent fraud and cyberattacks. They also help maintain a good reputation and build customer trust. Understanding these security measures is essential for anyone involved in online commerce. In this blog post, we will explore the key aspects of Payment Gateway Security Standards and why they matter for your business.
Credit: jatapp.co
Introduction To Payment Gateways
Payment gateways are essential for online transactions. They act as the bridge between the customer and the merchant. Understanding payment gateways is crucial for secure online business operations.
Role In Online Transactions
Payment gateways play a vital role in e-commerce. They process, authorize, and secure payments for online purchases. Here are some key functions:
- Encrypting sensitive information
- Facilitating payment authorizations
- Ensuring funds are transferred securely
Without these gateways, online transactions would be risky and inefficient. They provide the necessary infrastructure for smooth and safe payment processing.
Importance Of Security
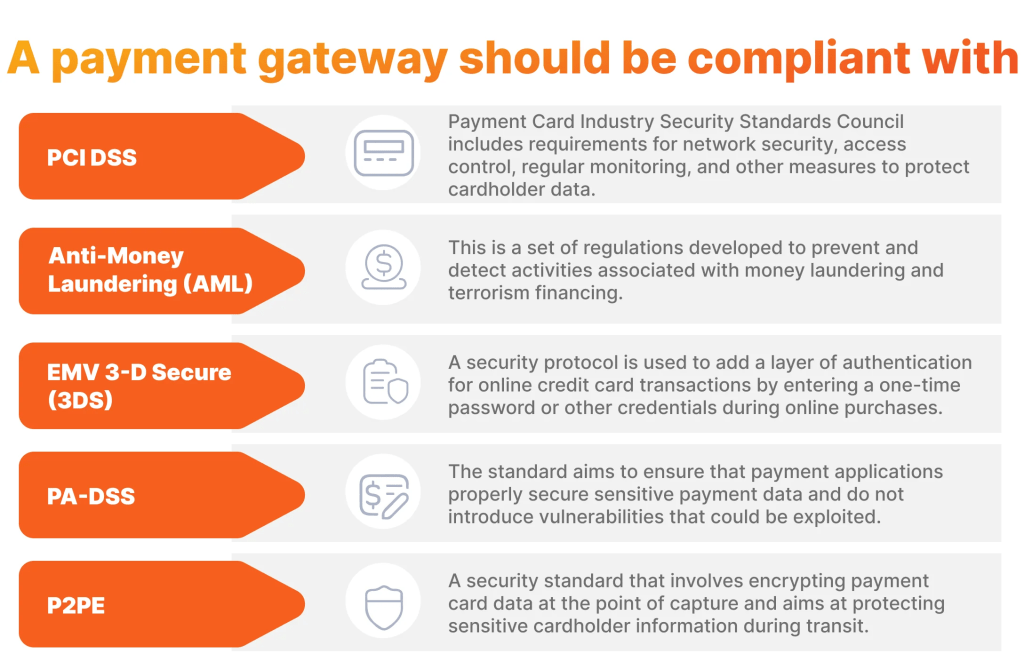
Security is paramount in online transactions. Payment gateways must comply with security standards to protect user data. Some important standards include:
| Standard | Description |
|---|---|
| PCI DSS | Payment Card Industry Data Security Standard. Ensures secure handling of card information. |
| SSL/TLS | Secure Sockets Layer/Transport Layer Security. Encrypts data transmitted over the internet. |
| 3D Secure | Three-Domain Secure. Adds an additional layer of security for online credit and debit card transactions. |
Compliance with these standards is essential. It helps in preventing data breaches and fraud. Customers trust businesses that ensure their data is protected. Thus, adhering to security standards is not just a requirement, but a responsibility.
Common Security Threats
In the digital world, payment gateways face many security threats. Understanding these threats helps businesses protect their customers. Below, we explore some common security threats that affect payment gateways.
Phishing Attacks
Phishing attacks are common threats to payment gateways. Cybercriminals use fake emails and websites to steal sensitive information. They trick users into giving their login details and credit card information. This can lead to financial loss and identity theft.
To protect against phishing attacks:
- Educate employees and customers about phishing scams.
- Use secure email filters to block suspicious emails.
- Implement two-factor authentication for added security.
Data Breaches
Data breaches are another major threat. Hackers gain unauthorized access to sensitive data. This includes credit card information, personal details, and transaction history. A data breach can damage a company’s reputation and lead to legal issues.
To prevent data breaches:
- Use encryption to protect sensitive data.
- Regularly update software and security systems.
- Conduct regular security audits to find vulnerabilities.
Pci Dss Compliance
Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards. These standards are designed to ensure that all companies that process, store, or transmit credit card information maintain a secure environment. Compliance with PCI DSS is crucial for safeguarding sensitive payment data.
Requirements Overview
To comply with PCI DSS, businesses must meet twelve main requirements. These requirements are grouped into six control objectives:
- Build and Maintain a Secure Network
- Install and maintain a firewall configuration to protect cardholder data.
- Do not use vendor-supplied defaults for system passwords and other security parameters.
- Protect Cardholder Data
- Protect stored cardholder data.
- Encrypt transmission of cardholder data across open, public networks.
- Maintain a Vulnerability Management Program
- Use and regularly update anti-virus software or programs.
- Develop and maintain secure systems and applications.
- Implement Strong Access Control Measures
- Restrict access to cardholder data by business need to know.
- Assign a unique ID to each person with computer access.
- Restrict physical access to cardholder data.
- Regularly Monitor and Test Networks
- Track and monitor all access to network resources and cardholder data.
- Regularly test security systems and processes.
- Maintain an Information Security Policy
- Maintain a policy that addresses information security for employees and contractors.
Benefits For Businesses
Adhering to PCI DSS brings several benefits to businesses:
- Enhanced Security: Protects against data breaches and fraud.
- Customer Trust: Builds confidence among customers about data protection.
- Compliance: Helps avoid fines and penalties associated with non-compliance.
- Operational Efficiency: Streamlines security processes and policies.
- Reputation Management: Reduces risk of damage to the business’s reputation.
These benefits make complying with PCI DSS not just a regulatory necessity but a strategic advantage.
Encryption Techniques
In the digital era, payment gateway security is crucial. Encryption techniques play a vital role in safeguarding transactions. Let’s delve into some key encryption methods that ensure secure online payments.
Ssl/tls Protocols
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) protocols are essential. They encrypt data between a user’s browser and the server. This ensures that sensitive information is protected during transit. SSL/TLS protocols use public and private keys to encrypt data. This makes it nearly impossible for hackers to intercept or read the data.
SSL/TLS also provides authentication. It verifies that the website is legitimate. Users see a padlock icon in their browser. This indicates a secure connection. It builds trust and confidence in the payment process.
End-to-end Encryption
End-to-End Encryption (E2EE) ensures that data is encrypted from the sender to the receiver. It is decrypted only by the recipient. This technique prevents unauthorized access during transmission. E2EE is vital for protecting sensitive payment information.
E2EE uses a combination of symmetric and asymmetric encryption. Symmetric encryption uses a single key for encryption and decryption. Asymmetric encryption uses a pair of keys – public and private. This dual approach enhances security.
Here’s a simple comparison table:
| Encryption Type | Key Characteristics |
|---|---|
| Symmetric Encryption | Single key for both encryption and decryption |
| Asymmetric Encryption | Public and private key pair for encryption and decryption |
E2EE is common in messaging apps. But it’s equally important in payment gateways. It ensures that only authorized parties can access payment details.
Encryption techniques like SSL/TLS protocols and E2EE are fundamental. They protect user data and secure transactions. Understanding these techniques helps in making safer online payments.
Tokenization
Tokenization is a method used in payment gateway security to protect sensitive data. It replaces sensitive data with unique identifiers or tokens. These tokens are meaningless if intercepted, ensuring that the original data remains safe.
How It Works
Tokenization works by replacing sensitive information with a unique identifier, known as a token. This token has no exploitable value. For example, a credit card number is replaced with a randomly generated string of characters. The actual credit card number is then stored securely in a token vault, separate from the token.
Here’s a simple process flow:
- User inputs sensitive data.
- Tokenization system generates a token.
- Original data is stored in a secure token vault.
- Token is used in transactions instead of the original data.
Advantages Over Encryption
Tokenization offers several advantages over encryption:
- Security: Tokens are meaningless if intercepted. They cannot be reverse-engineered.
- Simplicity: Tokenization is simpler to implement and manage. No complex encryption keys are needed.
- Compliance: Tokenization helps businesses meet compliance requirements such as PCI DSS. Sensitive data is never exposed.
- Performance: Tokenization can improve system performance. Tokens are smaller and quicker to process than encrypted data.
Tokenization reduces the risk of data breaches. Businesses can protect sensitive information efficiently.
Fraud Detection Tools
Payment gateways are crucial for online transactions. Ensuring their security is vital. One of the key components is using fraud detection tools. These tools help in identifying and preventing fraudulent activities. They use advanced technologies to keep transactions safe.
Machine Learning Algorithms
Machine learning algorithms are powerful in detecting fraud. They analyze vast amounts of data quickly. By identifying patterns, they can predict fraudulent activities. These algorithms get smarter over time. They learn from each transaction.
Here’s a simple example:
| Transaction Data | Algorithm Response |
|---|---|
| High-value purchase from a new location | Flag as suspicious |
| Multiple small transactions in a short time | Flag as suspicious |
Transaction Monitoring
Transaction monitoring is another essential tool. It involves continuous oversight of transactions. This process helps in real-time detection of unusual activities. Monitoring can include:
- Location of the transaction
- Frequency of purchases
- Changes in transaction patterns
Real-time alerts are crucial. They notify the system of any suspicious activities. This allows for immediate action to prevent fraud.
Here’s a quick checklist for effective transaction monitoring:
- Set up real-time alerts
- Review high-risk transactions
- Analyze transaction patterns regularly
Using these fraud detection tools can significantly enhance payment gateway security. It helps in building trust with customers by ensuring their transactions are safe.
Two-factor Authentication
Two-Factor Authentication (2FA) is a critical component in securing payment gateways. It adds an extra layer of security, ensuring that even if a password is compromised, unauthorized access is still prevented. This method requires users to verify their identity using two different factors. It is an essential practice in today’s digital world to protect sensitive payment information.
Implementation Methods
There are various methods to implement Two-Factor Authentication:
- SMS Verification: Users receive a code via text message.
- Email Verification: A verification link or code is sent to the user’s email.
- Authentication Apps: Apps like Google Authenticator generate time-based codes.
- Biometric Verification: Fingerprint or facial recognition for identity confirmation.
Different methods offer different levels of security and user convenience. It’s important to choose the right method based on the sensitivity of the payment gateway.
User Experience
Implementing Two-Factor Authentication can impact the user experience. The goal is to balance security and convenience:
- Ease of Use: Ensure the 2FA process is straightforward and easy to follow.
- Speed: The additional step should be quick, not causing delays in transactions.
- Support: Provide clear instructions and support for users facing issues.
Consider using a combination of methods to enhance both security and user experience. For instance, offering users a choice between SMS and authentication apps can cater to different preferences and needs.
Ultimately, a well-implemented Two-Factor Authentication system can significantly boost the security of payment gateways while maintaining a positive user experience.
Credit: www.nmi.com
Regulatory Compliance
Ensuring payment gateway security involves adhering to various regulatory compliance standards. These standards are designed to protect user data and maintain the integrity of financial transactions. Below, we discuss some critical regulatory frameworks.
Gdpr
The General Data Protection Regulation (GDPR) is a regulation in the European Union. It focuses on protecting personal data and privacy. GDPR compliance is vital for payment gateways operating within the EU.
Key GDPR requirements include:
- Data Protection by Design: Integrate data protection into system designs.
- Data Breach Notifications: Report breaches within 72 hours.
- User Consent: Obtain clear consent before processing user data.
Psd2
The Payment Services Directive 2 (PSD2) is another critical regulation in the EU. It aims to make electronic payments safer and more secure. PSD2 also fosters innovation and competition in the financial services sector.
PSD2 introduces several key requirements:
- Strong Customer Authentication (SCA): Requires two-factor authentication for transactions.
- Open Banking: Allows third-party providers to access bank data with user consent.
- Transaction Monitoring: Implements real-time monitoring to detect fraud.
Both GDPR and PSD2 are essential for maintaining payment gateway security. They ensure that user data is protected and financial transactions are secure.
Best Practices For Businesses
Implementing robust payment gateway security standards is crucial for businesses. It helps protect sensitive data and maintain customer trust. Adopting best practices can significantly reduce the risk of fraud and data breaches.
Employee Training
Employee training is essential for maintaining payment gateway security. Staff must understand the importance of protecting sensitive data. Regular training sessions can keep employees updated on the latest security threats and protocols.
- Conduct monthly security training sessions.
- Use real-life examples to illustrate security risks.
- Encourage employees to report suspicious activities immediately.
Regular Security Audits
Regular security audits are vital for identifying vulnerabilities in your payment gateway. They help ensure that your systems are compliant with industry standards and regulations.
| Audit Type | Frequency | Purpose |
|---|---|---|
| Internal Audits | Quarterly | Identify and fix internal vulnerabilities. |
| External Audits | Annually | Ensure compliance with industry standards. |
| Penetration Testing | Bi-annually | Test system security against external threats. |
Implementing these audits ensures your payment gateway remains secure and reliable.
Credit: magnetoitsolutions.com
Future Of Payment Gateway Security
The future of payment gateway security is a topic of immense importance. As digital transactions increase, ensuring secure payments is crucial. New technologies and trends are shaping the security landscape, making it essential to stay informed. Let’s explore the emerging technologies and trends to watch in payment gateway security.
Emerging Technologies
Emerging technologies promise to enhance payment gateway security. These advancements ensure safer transactions. Here are some key technologies to watch:
- Blockchain Technology: Blockchain provides a secure and transparent way to process payments. It reduces the risk of fraud by using distributed ledger technology.
- Artificial Intelligence (AI): AI helps detect fraudulent activities in real-time. It analyzes patterns and flags suspicious transactions.
- Biometric Authentication: Biometric methods, like fingerprint and facial recognition, offer secure user verification. They are harder to forge compared to traditional passwords.
- Tokenization: Tokenization replaces sensitive data with unique tokens. It minimizes the risk of data breaches.
Trends To Watch
Staying updated with the latest trends is vital for secure payment gateways. These trends highlight the direction of future security measures:
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple verification methods. It’s becoming a standard practice for secure transactions.
- Enhanced Encryption Techniques: Advanced encryption methods protect data during transmission. This ensures that only authorized parties can access the information.
- Regulatory Compliance: Compliance with regulations like GDPR and PCI DSS is mandatory. These regulations set standards for data protection and security.
- Real-Time Fraud Detection: Systems that detect and prevent fraud in real-time are crucial. They help in minimizing financial losses and protecting user data.
In summary, the future of payment gateway security depends on adopting new technologies and staying updated with the latest trends. These measures ensure secure and reliable digital transactions.
Frequently Asked Questions
What Are Payment Gateway Security Standards?
Payment gateway security standards are rules to protect online transactions. They ensure safe and secure payments.
Why Are Security Standards Important For Payment Gateways?
Security standards prevent fraud. They protect sensitive customer data and build trust in online transactions.
Which Security Standards Should Payment Gateways Follow?
Payment gateways should follow PCI-DSS, SSL/TLS encryption, and tokenization. These standards ensure high security levels.
How Does Pci-dss Improve Payment Security?
PCI-DSS sets strict security rules. It helps protect cardholder information and reduces the risk of data breaches.
What Is Ssl/tls Encryption?
SSL/TLS encryption secures data during transmission. It ensures that data remains private between the server and the client.
How Does Tokenization Work In Payment Security?
Tokenization replaces sensitive data with unique tokens. This protects real data from being exposed during transactions.
Can Payment Gateways Detect And Prevent Fraud?
Yes, many payment gateways use advanced tools. These tools detect suspicious activity and help prevent fraud.
Conclusion
Protecting payment information is crucial. Secure payment gateways build trust. They prevent fraud. Always choose gateways that meet security standards. Look for encryption and compliance. Regular updates and monitoring are essential. Keep your customers’ data safe. A secure gateway enhances customer confidence.
It also boosts your business reputation. Invest in security. It’s worth it. Stay informed on the latest security trends. This ensures your payment gateway remains reliable.